John the Ripper Detect Hash Type
This tutorial will dive into John the Ripper show you how it works and explain why you need it for security testing. John the Ripper is free and Open Source software distributed primarily in source code form.

John The Ripper Pro Password Cracker For Linux Distributor Reseller Resmi Software Original Jual Harga Murah Di Jakarta Melayani Se Indonesia
John The Ripper is an open source and very efficient password cracker by Open-Wall.

. Inline Non Staged A single payload containing the exploit and full shell code for the selected task. Several password cracking programs John the ripper for example apply some pattern matching on the input to guess the algorithm used but this only works on generic hashes. Find any available backups you have and consider keeping your data backups in secure off-site locations.
Therefore the higher the type of encryption 64-bit 128-bit or 256-bit encryption used to encrypt the password the longer it can take to break. You can try to use a Zip Password Recovery tool to safely recover. Brute force is also used to crack the hash and guess a password from a given hash.
John the Ripper jumbo - advanced offline password cracker which supports hundreds of hash and cipher types and runs on many operating systems CPUs. Hacker Type Description. It is very hard and may not be safe to crack zip password with scripts or codes.
John the Ripper jumbo - advanced offline password cracker which supports hundreds of hash and cipher types and runs on many operating systems CPUs GPUs and even some FPGAs - GitHub - openwalljohn. It is an Open Source tool and is free though a premium version also exists. Due to the evolution of password technologies the Open ware community develops and releases continuous.
Examples of wireless hacking tools include Aircrack. Its primary purpose is to detect weak Unix passwords although Windows LM hashes and a number of other password hash types are supported as well. Answer 1 of 12.
Metasploit contains many different types of payloads each serving a unique role within the framework. Today it supports cracking of hundreds of hashes and ciphers. For example if you take any hash output and rotate each letter by 1 most pattern matching schemes will fail.
This branch is pretty closely synced to hashcat git and John the Ripper git. Wireless hacking tools are used to intentionally hack into a wireless network to detect security vulnerabilities. The tool looks for encrypted logins complex ciphers and hash-type passwords.
No The Windows domain to use for authentication SMBPass no The password for the specified username. The tools are 100 compatible to hashcat and John the Ripper and recommended by hashcat. John the Ripper Pro password cracker.
John the Ripper is a fast password cracker available for many operating systems. Inline payloads are. While preparing the reference article Practical examples of John the Ripper usage the idea came up to make a similar article on Hashcat.
Kali Linux is preinstalled with over 600 penetration-testing programs including nmap a port scanner Wireshark a packet analyzer John the Ripper a password cracker Aircrack-ng a software. Return to the Passwords tab and see the password. Initially its primary purpose was to detect weak password configurations in Unix based Operating systems.
White Hat Hackers. Small set of tools convert packets from captures h hash c capture convert and calculate candidates x different hashtypes for the use with latest hashcat or John the Ripper. If you would instead try a commercial product tailored for your particular operating system please examine or look into John the Ripper Pro which is focused on distributing primarily in the native type packages for the target operating systems and usually.
John The Ripper password cracking utility brags of a user-friendly command-line interface and the ability to detect most password hash types. John the Ripper is also one of the Open Source Password Decoder Tools distributed primarily in source code form. John the Ripper was initially intended for use in Unix environments.
In this the hash is generated from random passwords and then this hash is matched with a target hash until the attacker finds the correct one. Proxies no A proxy chain of format typehostporttypehostport RECORD_GUEST false no Record guest-privileged random logins to the database RHOSTS yes The target address range or CIDR identifier RPORT 445 yes The SMB service port TCP SMBDomain. Those who regularly use Hashcat of course will be able to draw up the necessary mask at a glance and even remember the number of the frequently used hash type.
Follow edited Feb 27 2018 at 534. Click start attack to start the attack. Lets take a brief look at the various types of payloads available and get an idea of when each type should be used.
Leave a comment John the Ripper is a fast password cracker tool that supports UNIX Linux Windows and Mac OS. Examples of password cracking tools include John the Ripper Ophcrack L0phtCrack THC Hydra RainbowCrack and Medusa. However current works with other types of systems including Windows DOS and OpenVMS systems.
Crack Windows Password With John The Ripper A Helpful Tool

Kali Linux Tutorial Introduction To Parsero Vulnerability Analysis Tool Kali Linux Tutorials Linux Analysis
Cracking Password John The Ripper Vk9 Security
Cracking Password John The Ripper Vk9 Security
Tutorial Password Cracking Part 2 With John The Ripper Youtube

Password Cracker John The Ripper Jtr Examples Golinuxcloud

John The Ripper Cracking Passwords Manualdehacker Com

Password Cracking With John The Ripper Engineering Education Enged Program Section
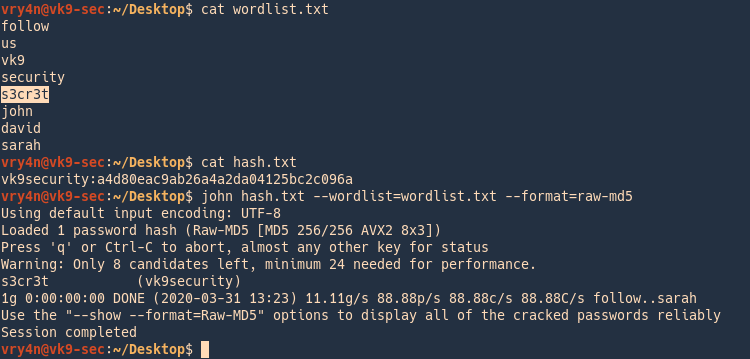
Cracking Password John The Ripper Vk9 Security

Basics Of John The Ripper Hash Testing Tool Tryhackme Complete Beginner Youtube

John The Ripper Installation And Crack Password
Cracking Password In Kali Linux Using John The Ripper Blackmore Ops

John The Ripper Fast Password Cracker Cyberpunk
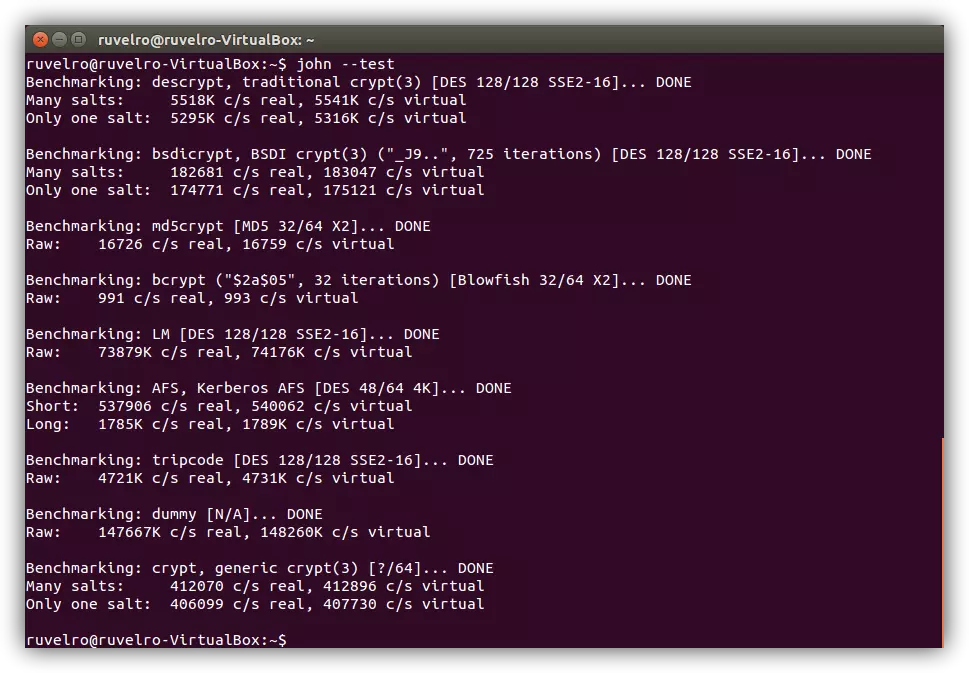
Crack Passwords Quickly Using John The Ripper

Playing With John The Ripper Kali Linux An Ethical Hacker S Cookbook

John The Ripper Penetration Testing Tools

John The Ripper Pentesting Tool For Offline Password Cracking To Detect Weak Passwords Cybercureme

John The Ripper Pentesting Tool For Offline Password Cracking To Detect Weak Passwords Cybercureme

Comments
Post a Comment